Data is viewed as the core asset of an enterprise. Preventing data leakage through traditional TDE and DLP methods is not only less efficient, putting bad effects on terminal and network performance, but also fail to offer fundamental guarantee for enterprise data and important information.
 Difficulty in data grading
Difficulty in data grading
 It's hard to strike a balance between
compatibility, efficiency and security
It's hard to strike a balance between
compatibility, efficiency and security
 Lack of flexible security
implementation
Lack of flexible security
implementation
 High cost and complicated process of operation
and maintenance
High cost and complicated process of operation
and maintenance
With a combination of identity management, AI security decision centers, lightweight trusted computing technologies, micro-segmentation and software-defined perimeters, AerospaceX’s self-adaptive secure zero-trust computing platform not only realize controllable access, stealth business and reduced exposure surface to keep away from cyber attacks, but also achieve environmental trust and data security in terminal devices and cloud computing nodes. By doing so, we enable security systems to meet the need of the digital business in a self-adaptive, automatic, clouding and mandatory way and comprehensively prevent internal and external security risks including data leakage, blackmail, network invasion, carrier theft, illegal operations, and software and hardware loophole.
 Clearer data boundaries
Clearer data boundaries
 The perfect balance between safety and
efficiency
The perfect balance between safety and
efficiency
 Lower security construction costs
Lower security construction costs
 More efficient implementation, operation and
maintenance
More efficient implementation, operation and
maintenance
VPN for a company is limited to access to certain applications and businesses are confronted with huge terminal security risks after it operates owing to concerns about data leakage and network intrusion. AerospaceX assists businesses to fully embrace zero-trust network access, realizing consistent security control domestically and overseas to enhance productivity.
 VPN causes intranet
exposure and fails to limit authority precisely
VPN causes intranet
exposure and fails to limit authority precisely
 Censorship risks of
outbound and cross-border data
Censorship risks of
outbound and cross-border data
 Fails to build
dynamic terminal security that prevents intrusion and penetration
Fails to build
dynamic terminal security that prevents intrusion and penetration
 Risk of data
leakage due to carrier loss
Risk of data
leakage due to carrier loss
 It is difficult to
effectively control the data and secondary distribution after the launch of a business.
It is difficult to
effectively control the data and secondary distribution after the launch of a business.
AerospaceX self-adaptive security computing platform realizes borderless access and operation protection of business globally: The risk of remote invasion is prevented from moving laterally in the intranet by conducting micro-segment on remote cloud service via micro-segment containers of AerospaceX; Remote business is stealthily and flexibly connected in the network by zero-trust security gateway; the terminal self-adaptive security computing environment makes it possible to build a controllable digital space on a remote device, where there is a direct connection with enterprise internal servers and are business that is "accessible, not invadable" and data that is "computable, not accessible".

 Agile deployment with more
flexible architecture and available cross-site collaboration
Agile deployment with more
flexible architecture and available cross-site collaboration
 Data leakage and remote
intrusion are prevented with more secure terminal control
Data leakage and remote
intrusion are prevented with more secure terminal control
 Trusted network boundaries
created by VPN is no longer needed with more secure network
Trusted network boundaries
created by VPN is no longer needed with more secure network
 Office habits changes are
no longer needed with more stable experience and low-performance impact
Office habits changes are
no longer needed with more stable experience and low-performance impact
VDI leads to problems such as lagging experience, high construction cost and lack of security capability. The next-generation desktop security control solution provided by AerospaceX creates an elastic and secure computing desktop with upgraded performance and experience, significantly reducing customer costs while improving user experience.
The wrong assumption about threats for information security in China currently remains the biggest problem as people invariably associate risks with external attacks while 80% of information leakage is actually the result of internal or the combination of internal and external attacks. From the perspective of a business, information including core technologies and data of main customers, market, and financial reports is where its competitiveness comes from. As Cybersecurity Insiders: Insider Threats puts, today's most damaging security threats are not originating from malicious outsiders or malware but from trusted insiders—both malicious insiders and negligent insiders; According to The Ministry of Public Security of the People's Republic of China,70% of information leakage is caused by a business' insiders.
It has been a key concern for a business to find ways to standardize the operation procedures, take precautionary measures, monitor and give alarms when an emergency arises, and audit and trace back network vulnerabilities.
Hence, management on mandating users' operation in line with industry standards by virtue of effective technologies and professional tools is essential. Therefore, operations of insiders have rules to follow, which means the realization of behavior audibility and traceability, contributing to the visualization of internal threats management.
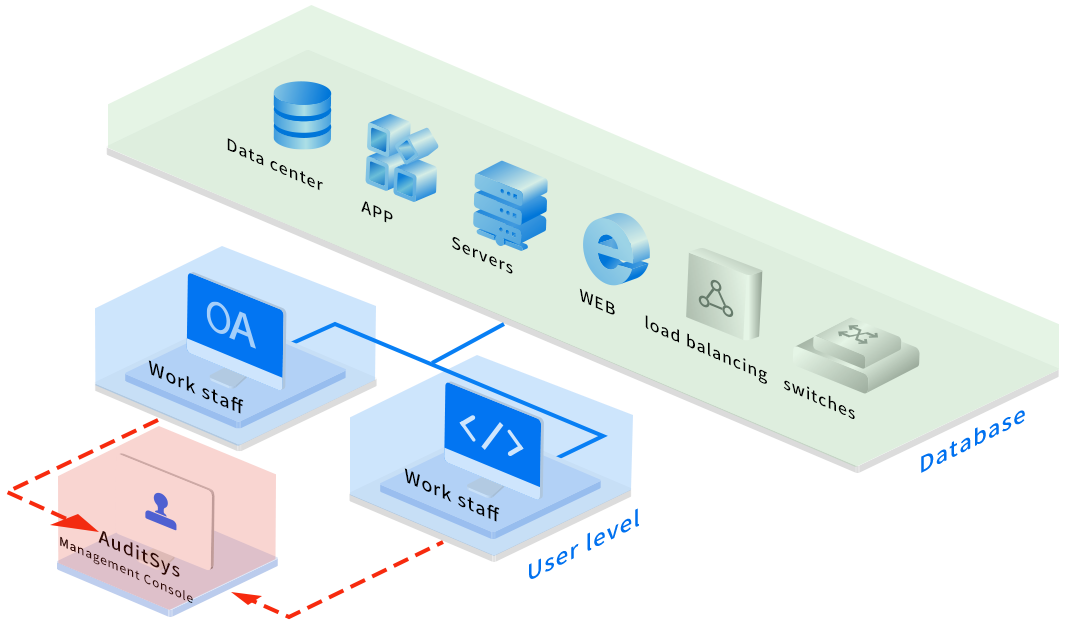
AuditSys features functions of behavior classification display, behavior traceability, and fine-grained behavioral retrieval by taking access to all operational data of terminal users and saving them with words and screen recordings. As such, it’s able to identify risks emerging at a specific time and to provide valid evidence for performing accountability if there are any violations of corporate interests.
The platform has nearly 100 behavioral rules to prevent risks, which customers can mandate or customize according to their own needs. Therefore, irregular operations with high risks including user's overstepping and data breaches, and potential risk behaviors in a business system can be effectively targeted. Subsequently, terminal users will be informed and educated to raise their security awareness and be instructed to standardize operations.
Meanwhile, centralized architecture and distributed architecture are both available in AuditSys. As these architectures are easy to lay out and can be flexibly applied to different scenarios in a business without reshaping the existing IT architecture, they help the digital transformation of corporations, realizing the visualization of behaviors and risks.
 Behavioral audit traceability
Behavioral audit traceability
 Risk monitoring of business operations
Risk monitoring of business operations
 Regulated user operations
Regulated user operations
 Improved business security
Improved business security
The social economy is embracing the era of big data with the rapid development of information technology. Yet, as a great deal of sensitive data and personal information collected on the business system is vulnerable to external and internal attacks, information abuse, leakage or malicious tampering have been emerging, exerting negative impacts at different levels on users, society even the whole country. In this context, it is an emerging challenge to provide a sound environment and refined data security control strategy for users based on connectivity, interoperability, and date opening and sharing.
 Huge challenges to
meet the standard
Huge challenges to
meet the standard
 Unclear user data
classification and grading
Unclear user data
classification and grading
 High-cost
supervision of a large amount of flowing data
High-cost
supervision of a large amount of flowing data
 Unauthorized access
made by internal personnel and stealth of data committed by external hackers
Unauthorized access
made by internal personnel and stealth of data committed by external hackers
 Difficulty to
redevelop applications for increasing security
Difficulty to
redevelop applications for increasing security
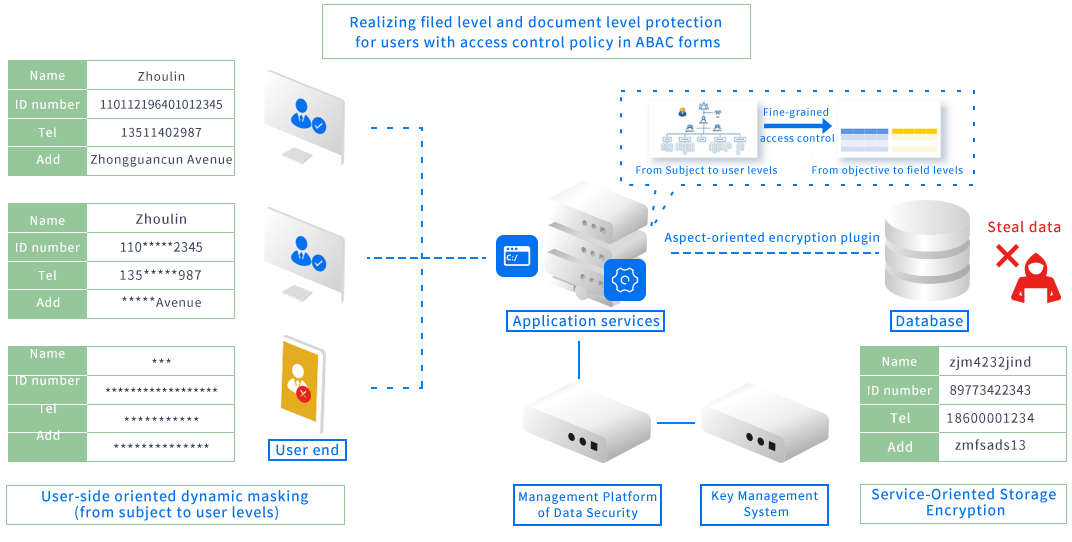
CASB business data encryption platform deals with application system protection and agilely implemented data encryption. It's capable of encrypting the database at any specified field (to prevent IT insiders and external hackers) by using aspect-oriented encryption plugins with only configuration-level deployment rather than any source code modification. Meanwhile, it has realized dynamic masking and audit of data covering user's information (to prevent business insiders from overstepping their authorities), and realized supervision, identification and grading with the assistance of a data identification engine during the process of data flow. This platform is adaptive to typical protection scenarios at individual, business and national levels such as personal information, business commercial secrets and confidential instructions made by the central government including rectifying government, state-owned business, and finance industry.